Nearly half of all American organizations have experienced an insider security incident within the past year, revealing a growing threat that often goes unnoticed until it is too late. For professionals in Miami, where fast-paced business and diverse teams are the norm, these risks are amplified by high employee turnover and inconsistent training. Understanding how insider threats develop and how they bypass traditional safeguards equips you with the insight needed to keep your data and reputation safe.
Table of Contents
- Insider Threats Explained for Miami Professionals
- Types of Insider Threats Affecting Firms
- Warning Signs and Risk Factors to Watch
- Legal and Compliance Implications in Miami
- Best Practices for Cyber Awareness Training
Key Takeaways
| Point | Details |
|---|---|
| Insider Threats Are Complex | Miami organizations face significant risks from insider threats that can be malicious or accidental, making detection and prevention challenging. |
| Robust Prevention Strategies Are Essential | Implementing access controls, regular training, and clear data handling policies can effectively mitigate insider threats. |
| Recognizing Warning Signs Is Crucial | Monitoring for unusual behavior and technical indicators helps identify potential insider threats before they escalate. |
| Legal Compliance Is Necessary | Adhering to data protection regulations and establishing a culture of security awareness is vital for minimizing legal risks associated with insider threats. |
Insider Threats Explained for Miami Professionals
When it comes to cybersecurity, insider threats represent one of the most unpredictable and dangerous risks facing Miami businesses today. Unlike external hackers, insiders already have authorized access to your systems, making their potential for damage significantly more complex and challenging to detect. Cybersecurity experts confirm that insider threats can bypass many traditional firm controls, creating substantial vulnerabilities for organizations.
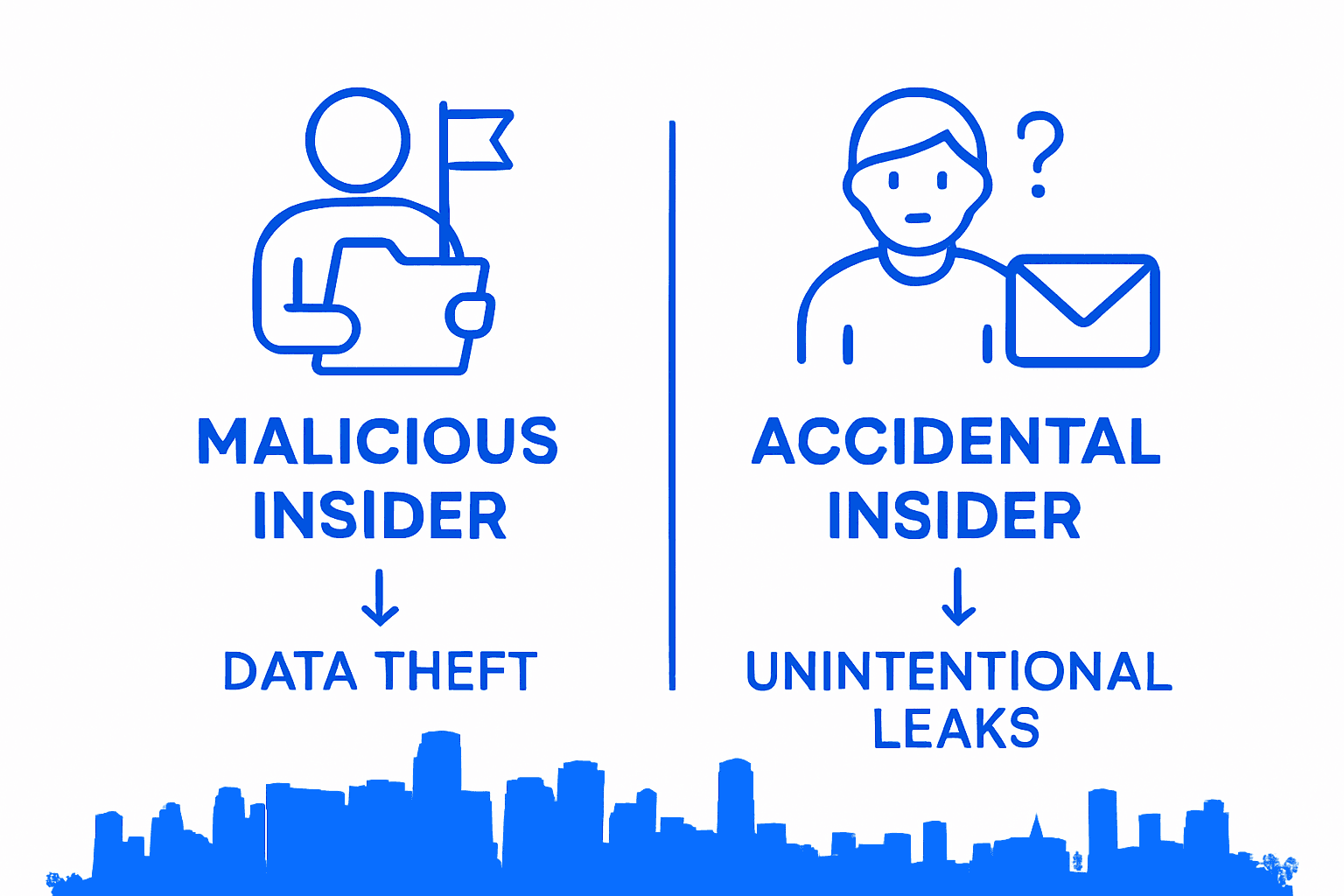
Insider threats come in two primary forms: malicious and accidental. Malicious insider threats occur when an employee intentionally seeks to harm the organization, potentially stealing sensitive data or sabotaging systems. Accidental threats happen when well-meaning employees make mistakes like falling for phishing emails, using weak passwords, or accidentally sharing confidential information. Miami’s diverse business landscape makes these risks particularly acute, with high employee turnover and inconsistent cybersecurity training amplifying potential vulnerabilities.
To effectively mitigate insider threats, Miami professionals need a multi-layered approach. This includes implementing robust access controls, conducting regular security awareness training, monitoring user activities, and creating clear protocols for data handling. Organizations should develop comprehensive strategies that balance technological solutions with human-centric policies, recognizing that employees can be both the greatest security risk and the most important line of defense.
Pro Security Strategy: Create a clear, written insider threat prevention policy that outlines acceptable technology use, consequences for violations, and mandatory annual cybersecurity training for all team members.
Types of Insider Threats Affecting Firms
Insider threats are not a one-size-fits-all problem. In reality, they manifest in complex and nuanced ways that can devastate organizational security. Cybersecurity experts identify two primary categories of insider threats: intentional and unintentional actions that can lead to severe consequences, each presenting unique challenges for Miami firms.
Malicious insider threats represent the most dangerous category. These occur when employees deliberately attempt to harm the organization, often motivated by financial gain, revenge, or personal grievances. Deliberate actions might include selling sensitive customer data on the dark web, intentionally introducing malware, or sabotaging critical systems. Financial firms face particularly acute risks, with potential threats ranging from selling customer account information to deliberately compromising security protocols.
Unintentional insider threats are equally problematic, stemming from employee negligence or lack of awareness. These can involve accidentally sharing confidential information, using weak passwords, falling for phishing emails, or failing to follow established security protocols. Such mistakes might seem minor but can create significant vulnerabilities that sophisticated cybercriminals can exploit. Miami businesses must recognize that these unintentional threats often pose as much risk as deliberate attacks, making comprehensive employee training crucial.
Here’s a concise summary of the primary types of insider threats for Miami firms:
| Threat Type | Common Motivations | Typical Actions | Potential Impact |
|---|---|---|---|
| Malicious Insider | Financial gain, revenge | Data theft, sabotage, fraud | Major financial and reputational loss |
| Accidental Insider | Human error, negligence | Data leaks, weak passwords | Unauthorized access, data breaches |
Pro Security Insight: Develop a comprehensive insider threat awareness program that educates employees about both intentional and unintentional risks, combining technical training with clear, actionable security guidelines that employees can easily understand and implement.
Warning Signs and Risk Factors to Watch
Insider threat detection requires vigilant monitoring and a proactive approach to identifying potential risks before they escalate. Cybersecurity professionals recommend carefully tracking unusual behavioral patterns and technological indicators that might signal an impending insider threat, providing organizations with critical early warning mechanisms.
Several key risk factors can significantly increase an organization’s vulnerability to insider threats. High employee turnover, inadequate cybersecurity training, and poor access control management are fundamental indicators that can dramatically elevate internal breach potential. Warning signs often manifest through specific behavioral and technical signals, such as employees accessing systems outside their normal work hours, downloading unusually large volumes of data, attempting to bypass security protocols, or showing sudden changes in work performance and attitude.
Technical indicators represent another crucial dimension of insider threat detection. Organizations should watch for red flags like unauthorized database queries, attempts to install unauthorized software, repeated failed login attempts, or attempts to escalate user privileges without proper authorization. Employees who demonstrate persistent curiosity about security systems, consistently request access to information outside their job responsibilities, or show resistance to standard security protocols may also be potential risk indicators that warrant closer examination.
Pro Security Strategy: Implement a comprehensive threat monitoring system that combines behavioral analytics, access log monitoring, and regular security awareness training to create a proactive defense against potential insider threats.
Legal and Compliance Implications in Miami
Miami businesses face a complex landscape of legal responsibilities when it comes to cybersecurity and insider threats. Law firms and professional organizations must navigate stringent data protection regulations like GDPR and CCPA, with potential non-compliance resulting in substantial financial penalties and serious legal consequences, making proactive security measures absolutely critical.
Professional ethical standards play a pivotal role in defining legal obligations around data protection. The Florida Bar’s Professional Ethics Rules explicitly mandate that lawyers make reasonable efforts to prevent unauthorized access to client information, establishing a clear legal framework for cybersecurity practices. This requirement extends beyond mere technical compliance, demanding a comprehensive approach to protecting sensitive client data from potential insider threats.
The legal implications of insider threats go far beyond immediate financial risks. Organizations can face significant liability for data breaches, potential lawsuits from affected clients, regulatory investigations, and long-term reputational damage. Miami firms must recognize that their legal exposure isn’t just about preventing immediate financial losses, but also about maintaining the trust and confidentiality that are fundamental to professional services. This means implementing robust security protocols, conducting regular risk assessments, and creating a culture of security awareness that meets both ethical and legal standards.
Pro Legal Defense Strategy: Develop a comprehensive documentation process that tracks all cybersecurity measures, training efforts, and incident response protocols, creating a defensible record of your organization’s commitment to protecting client information.
Best Practices for Cyber Awareness Training
Cyber awareness training represents a critical defense mechanism against insider threats, transforming employees from potential vulnerabilities into active security partners. Comprehensive cybersecurity training programs must go beyond basic instruction, focusing on recognizing sophisticated phishing attempts, implementing secure data handling practices, and understanding the critical importance of reporting suspicious activities, creating a proactive security culture within organizations.
Effective insider threat mitigation requires implementing strategic monitoring techniques, including role-based access control, continuous auditing, and advanced data loss prevention tools. Training programs should incorporate practical, scenario-based learning that helps employees understand real-world cyber risks. This means developing interactive modules that simulate potential insider threat situations, teaching staff how to recognize red flags, and providing clear protocols for reporting potential security breaches.
Successful cyber awareness training must be dynamic and continuously evolving. Organizations should develop multi-tiered training approaches that include initial onboarding sessions, periodic refresher courses, and ongoing education about emerging cyber threats. These programs should be tailored to different organizational roles, recognizing that technical staff, management, and administrative personnel face unique cybersecurity challenges. Gamification, real-world case studies, and interactive workshops can transform dry security training into engaging learning experiences that truly resonate with employees.
This table outlines effective measures for reducing insider threat risks in Miami organizations:
| Prevention Measure | What It Does | Business Benefit |
|---|---|---|
| Role-based access controls | Limits sensitive data exposure | Minimizes unauthorized disclosures |
| Continuous employee training | Educates staff on risks | Reduces accidental data breaches |
| Monitoring user activities | Detects unusual behavior | Enables early threat detection |
| Clear data handling policies | Standardizes security practices | Strengthens compliance and trust |
Pro Training Strategy: Create a mandatory annual cybersecurity certification program that requires employees to demonstrate practical knowledge of insider threat recognition, reporting mechanisms, and basic security protocols through interactive assessment modules.
Strengthen Your Miami Firm Against Insider Threats Today
Insider threats present a unique and pressing challenge for Miami businesses, especially for Doctors, Lawyers, and Accountants who handle sensitive client data daily. From detecting unusual employee behavior to enforcing strict access controls, the risks are real and evolving. Protecting your firm means addressing these threats proactively with proven strategies like role-based access, continuous monitoring, and tailored cybersecurity training.
Take control by partnering with experts who understand these risks deeply and help you build the security framework your clients expect. Explore practical solutions in our Security Archives – Strategic IT Consultants For Accountants and discover how we empower firms like yours to land bigger clients and scale without extra hires. Don’t wait for a breach to act. Visit our website now and start transforming your cybersecurity posture into a competitive advantage.
Frequently Asked Questions
What are the types of insider threats that Miami firms face?
Miami firms face two primary types of insider threats: malicious and accidental. Malicious threats involve deliberate harmful actions by employees, while accidental threats arise from employee negligence or lack of awareness.
How can organizations in Miami effectively mitigate insider threats?
To mitigate insider threats, Miami organizations should implement robust access controls, conduct regular security awareness training, monitor user activities, and establish clear protocols for data handling.
What warning signs should firms monitor for potential insider threats?
Firms should watch for unusual behavioral patterns, such as accessing systems outside normal hours, downloading large volumes of data, and requests for access to information unrelated to job responsibilities. Technical indicators like unauthorized database queries and failed login attempts are also key signs.
What legal implications do insider threats have for businesses?
Businesses may face significant liability for data breaches caused by insider threats, including potential lawsuits, regulatory investigations, and reputational damage. Compliance with data protection regulations and professional ethical standards is essential to avoid these risks.
Recommended
- Securing the Defense Industry: Tackling Cybersecurity in an Interconnected World
- Complete Guide to Cyber Security for Miami CPAs
- Complete Guide to Cyber Security for Miami CPAs – Stratgetic IT Consultants for Accountants
- Cybersecurity: The Greatest Threat Facing Today’s Defense Industry and Why It’s So Tough to Defend Against
- The Essential Guide to Cannabis Business Risk Management – Cannabis Business Minds