Most American accounting firms underestimate just how vulnerable their financial data is to cyber threats. With more than 60 percent of organizations reporting at least one cybersecurity incident each year, weak points in technology or simple human mistakes can put sensitive information at risk. Understanding how vulnerabilities are exploited is essential for American professionals who manage confidential records and rely on client trust to build lasting business relationships.
Table of Contents
- Defining Vulnerability In Cybersecurity Context
- Types Of Vulnerabilities Affecting CPA Firms
- How Cyber Attackers Exploit Weaknesses
- Regulatory Compliance And Reporting Obligations
- Practical Strategies To Minimize Cyber Risks
Key Takeaways
| Point | Details |
|---|---|
| Understanding Vulnerabilities | Cybersecurity vulnerabilities represent critical weak points that can compromise sensitive data and systems, requiring a proactive approach to management. |
| Types of Vulnerabilities in CPA Firms | CPA firms face vulnerabilities from technical threats, social engineering, and human errors, necessitating comprehensive protective measures. |
| Combatting Exploitation Techniques | Cyber attackers exploit both technological flaws and human behavior; awareness and training are key in preventing breaches. |
| Importance of Compliance | Regulatory compliance mandates that CPA firms implement robust cybersecurity measures and maintain rigorous reporting standards to protect client trust. |
Defining Vulnerability In Cybersecurity Context
In the world of accounting and financial services, cybersecurity vulnerability represents a critical weak point that could potentially expose sensitive client data and organizational systems to unauthorized access or malicious attacks. Unlike physical security breaches, these vulnerabilities are often invisible yet incredibly destructive.
Cybersecurity experts recognize that vulnerabilities are not just technical issues but complex interactions between technology, processes, and human behavior. Comprehensive cyber defense strategies must address weaknesses across multiple dimensions. According to research from academic and government sectors, vulnerabilities encompass three primary domains: technical infrastructure, operational procedures, and human factors.
At its core, a cybersecurity vulnerability represents any systemic weakness that could be exploited by threat actors. These might include outdated software, misconfigured network settings, weak password protocols, or insufficient employee training. For Miami CPAs handling sensitive financial records, understanding these potential entry points is not just about technology – it’s about protecting client trust and professional reputation. The potential consequences range from data theft to complete system compromise, making proactive vulnerability assessment a critical business imperative.
Key characteristics of cybersecurity vulnerabilities include:
- Potential for unauthorized system access
- Ability to compromise data confidentiality
- Risk of operational disruption
- Potential financial and reputational damage
Successful vulnerability management requires continuous monitoring, regular system assessments, and a holistic approach that treats cybersecurity as an ongoing strategic priority rather than a one-time technical fix.
Types Of Vulnerabilities Affecting CPA Firms
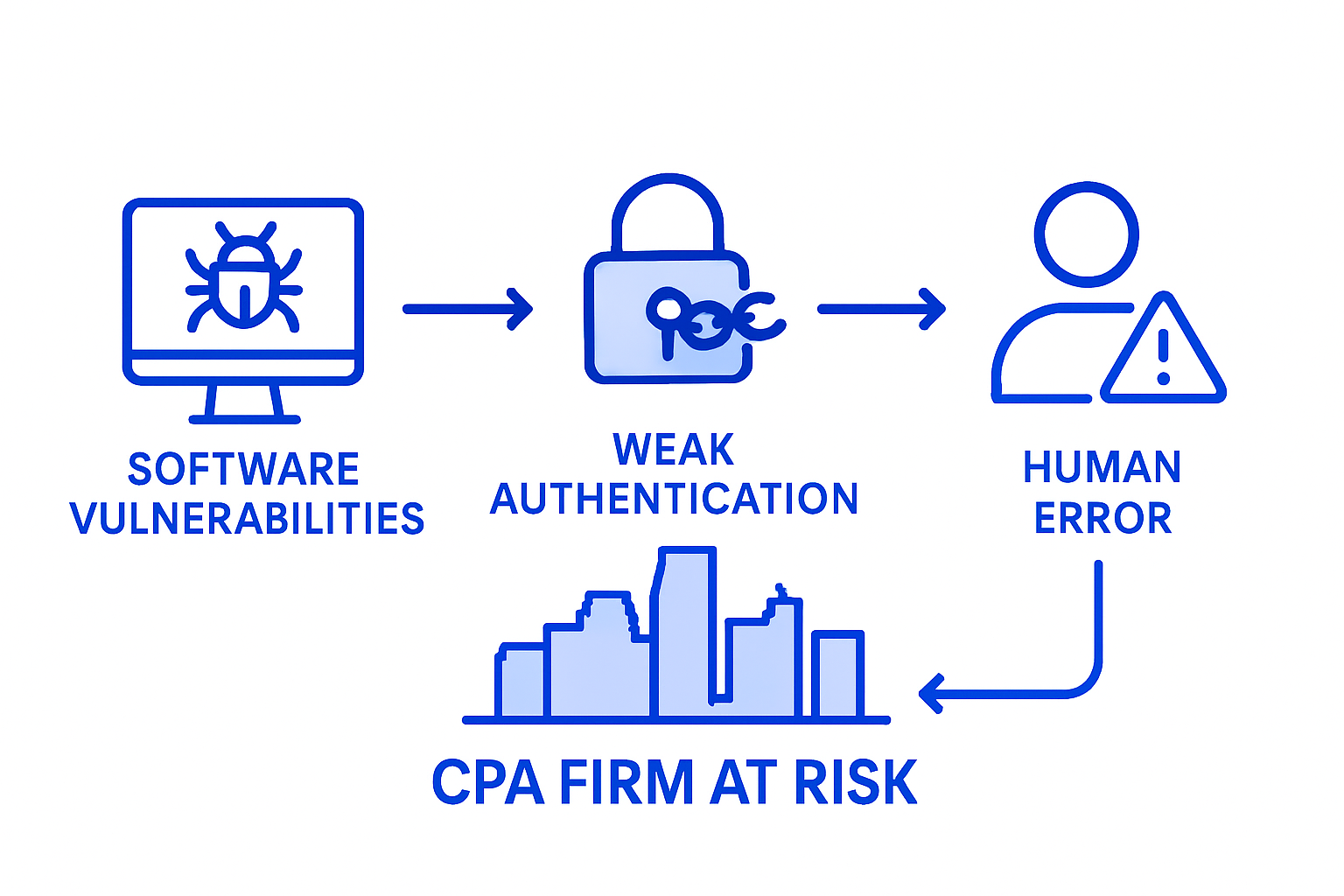
CPA firms face a complex landscape of cybersecurity vulnerabilities that can compromise sensitive financial data and client confidentiality. These vulnerabilities are not just technical glitches but sophisticated threats that can penetrate even well-defended organizational systems.
Social engineering attacks represent a critical vulnerability for accounting professionals. These sophisticated tactics manipulate human psychology, tricking employees into revealing confidential information or granting unauthorized system access. Phishing emails disguised as legitimate client communications, fraudulent password reset requests, and impersonation schemes are particularly dangerous for CPAs handling sensitive financial records.
Technical vulnerabilities also pose significant risks to accounting firms. Outdated software, unpatched systems, weak network configurations, and inadequate access controls can create entry points for cybercriminals. Accounting firms often manage complex digital ecosystems with multiple interconnected systems, which increases potential attack surfaces. Specific technical vulnerabilities include:
- Unpatched software with known security gaps
- Misconfigured cloud storage settings
- Weak authentication protocols
- Inadequate encryption for sensitive financial documents
- Insufficient network segmentation
Human-factor vulnerabilities remain the most unpredictable and challenging to address. Employee mistakes, lack of cybersecurity awareness, and insufficient training can inadvertently create significant organizational risks. Simple actions like clicking suspicious links, using weak passwords, or failing to recognize social engineering tactics can expose entire accounting firms to potential breaches.
How Cyber Attackers Exploit Weaknesses
Cyber attackers are sophisticated digital predators who meticulously hunt for system vulnerabilities like skilled hunters tracking prey. Their strategies are complex, targeting both technological weaknesses and human psychological blind spots to gain unauthorized access to sensitive information.
Cybercriminals exploit intrinsic and extrinsic vulnerabilities with surgical precision. Intrinsic vulnerabilities include technical flaws like unpatched software, misconfigured network settings, and outdated security protocols. Extrinsic vulnerabilities focus on human behavior – leveraging psychological manipulation, social engineering tactics, and employee negligence to breach organizational defenses.
The attack methodology typically follows a calculated progression. Attackers first conduct reconnaissance, mapping out potential entry points within an organization’s digital infrastructure. They identify weak authentication mechanisms, examine outdated software versions, and probe network configurations for potential exploits. Key exploitation techniques include:
- Phishing email campaigns
- Credential harvesting
- Malware deployment
- Exploiting unpatched software vulnerabilities
- Manipulating access control systems
Human error remains the most significant vulnerability. A single misclicked link, a momentary lapse in judgment, or an improperly secured password can provide cybercriminals with the golden ticket to infiltrate entire organizational networks. For accounting firms handling sensitive financial data, understanding these exploitation techniques is not just a technical requirement but a critical business survival strategy.
Regulatory Compliance And Reporting Obligations
Cybersecurity compliance for accounting firms represents a complex web of legal and professional responsibilities that extend far beyond simple technological safeguards. Regulatory requirements demand comprehensive strategies to protect sensitive financial data and maintain client trust.
Firms must navigate intricate reporting obligations mandated by regulatory bodies like FINRA and the SEC. These regulations require prompt disclosure of cybersecurity incidents, maintenance of rigorous data protection protocols, and implementation of robust risk management frameworks. Specific compliance requirements include:
- Immediate reporting of potential security breaches
- Documenting cybersecurity risk assessments
- Maintaining comprehensive incident response plans
- Protecting client information with advanced security measures
- Conducting regular vulnerability assessments
Third-party vendor management represents another critical compliance dimension. Accounting firms are increasingly responsible for ensuring that their technology partners and service providers maintain equivalent cybersecurity standards. A single vulnerability in a third-party system can compromise an entire organization’s data integrity, potentially triggering significant legal and financial consequences.
The stakes are high for Miami CPA firms. Non-compliance can result in substantial financial penalties, loss of professional licenses, reputational damage, and potential legal action from affected clients. Proactive compliance is not just a regulatory requirement but a fundamental business survival strategy in today’s increasingly complex digital landscape.
Practical Strategies To Minimize Cyber Risks
Cybersecurity is not a one-time investment but a continuous process of vigilance and strategic planning for Miami CPA firms. Proactive risk management requires a multi-layered approach that addresses technological, human, and procedural vulnerabilities.
Implementing secure remote access protocols becomes critical in today’s distributed work environments. Specific strategies include:
- Using virtual private networks (VPNs) for encrypted connections
- Establishing secure client file-sharing portals
- Encrypting emails containing confidential financial information
- Implementing multi-factor authentication
- Restricting administrative access privileges
Employee training represents the most crucial line of defense against cyber threats. Accounting professionals must develop a culture of cybersecurity awareness, understanding that human behavior can be the weakest link in organizational defense. This involves regular training on recognizing phishing attempts, maintaining strong password hygiene, and understanding the potential consequences of seemingly minor security lapses.
Technical safeguards must be complemented by strategic risk management. This includes obtaining comprehensive cyber insurance, conducting regular vulnerability assessments, and developing robust incident response plans. For Miami CPA firms, cybersecurity is not just about preventing breaches but maintaining the fundamental trust that is the cornerstone of their professional relationships.
Protect Your Miami CPA Firm From Cybersecurity Vulnerabilities Today
Cybersecurity vulnerabilities put your accounting firm at serious risk. From unpatched software to social engineering attacks these weaknesses threaten client data confidentiality and regulatory compliance. If you are a Miami CPA committed to preserving your firm’s professional reputation and avoiding costly disruptions now is the time to take action. At Transform42 we understand that proactive vulnerability management means more than technology—it means aligning cybersecurity strategy with your business goals for total peace of mind.
Discover how our ironclad compliance solutions and 99.99% uptime reliability eliminate security risks and prevent regulatory penalties. Do not wait for a breach or legal trouble to force your hand. Visit Transform42 now and protect your firm with guaranteed 15-minute response times backed by our promise—you do not pay if we do not deliver. Start securing your CPA firm’s future today.
Frequently Asked Questions
What are the main types of cybersecurity vulnerabilities that affect CPA firms?
Common cyber vulnerabilities for CPA firms include social engineering attacks, outdated software, weak authentication protocols, and human-factor vulnerabilities due to insufficient employee training.
How do cyber attackers exploit vulnerabilities in CPA firms?
Cyber attackers exploit vulnerabilities by conducting reconnaissance to identify weak points, utilizing techniques like phishing campaigns, credential harvesting, and exploiting unpatched software vulnerabilities to gain unauthorized access to sensitive information.
What are the compliance obligations for CPA firms regarding cybersecurity?
CPA firms must adhere to regulatory requirements that include immediate reporting of security breaches, implementing data protection protocols, and maintaining incident response plans, along with ensuring their third-party vendors have comparable cybersecurity standards.
How can CPA firms minimize cyber risks effectively?
CPA firms can minimize cyber risks by implementing secure remote access protocols, conducting regular employee training on cybersecurity awareness, performing vulnerability assessments, and having robust incident response plans in place.