Cyber attacks cost the average American accounting firm over $200,000 in damages each year. When financial data is on the line, even a single breach can destroy hard-earned trust with clients. Protecting your Miami CPA practice means going far beyond basic antivirus software. This guide shows practical steps to assess vulnerabilities, train your team, and implement real-world defenses that every American accounting firm needs.
Table of Contents
- Step 1: Assess Current Cyber Security Risks And Vulnerabilities
- Step 2: Develop Tailored Awareness Training For Your Team
- Step 3: Implement Security Policies And Practical Safeguards
- Step 4: Reinforce Learning With Simulated Phishing Exercises
- Step 5: Verify Progress Through Periodic Assessment And Feedback
Quick Summary
| Key Insight | Explanation |
|---|---|
| 1. Conduct comprehensive risk assessments | Identify and evaluate vulnerabilities to protect against cyber threats effectively. |
| 2. Tailor cybersecurity training for staff | Develop relevant training modules that address specific cybersecurity risks faced by accountants. |
| 3. Implement robust security policies | Establish clear guidelines and protocols to safeguard sensitive financial data consistently. |
| 4. Use simulated phishing exercises | Train employees by mimicking real-world phishing threats to enhance their response capabilities. |
| 5. Assess cybersecurity progress regularly | Periodically evaluate performance metrics and adjust strategies to improve overall security posture. |
Step 1: Assess current cyber security risks and vulnerabilities
Understanding your accounting firm’s cyber security landscape starts with a comprehensive risk assessment. This crucial process helps you identify potential vulnerabilities before cybercriminals can exploit them. Developing a systematic mission centric approach to estimate security infrastructure risks will give you a strategic advantage in protecting sensitive financial data.
Begin by conducting a thorough inventory of all digital assets and systems your Miami CPA practice uses. This includes computers, networks, cloud storage, client management software, and communication platforms. Map out how data flows through these systems and identify potential weak points. Pay special attention to areas where sensitive financial information could be exposed like email communications, client portals, tax preparation software, and remote access tools.
Next, perform a detailed vulnerability scan using professional cybersecurity assessment tools. Look for outdated software, unpatched systems, weak password protocols, and potential entry points for unauthorized access. Consider simulating potential breach scenarios to understand how an attacker might target your specific accounting infrastructure. This proactive approach allows you to prioritize and address the most critical security gaps before they become actual threats.
Pro tip: Create a living document that tracks all identified risks, their potential impact, and recommended mitigation strategies. Update this document quarterly to ensure your cybersecurity defenses remain current and robust.
Here’s a summary of essential cybersecurity assessment tools and their primary impact for accounting firms:
| Tool Type | Main Function | Business Impact |
|---|---|---|
| Asset Inventory Software | Catalogs all hardware and data | Improves visibility and management |
| Vulnerability Scanners | Detects unpatched weaknesses | Reduces risk of exploitation |
| Threat Simulation Tools | Imitates cyberattack scenarios | Reveals real-world system vulnerabilities |
| Risk Management Platforms | Tracks and prioritizes risks | Enables targeted and efficient defense |
Step 2: Develop tailored awareness training for your team
Crafting an effective cybersecurity awareness program for your Miami accounting firm requires a strategic and personalized approach. Your goal is to transform your team from potential security vulnerabilities into proactive defenders of sensitive financial information. How to Improve Cybersecurity for Miami Accounting Firms highlights the importance of creating targeted educational experiences that resonate with accounting professionals.
Start by developing training modules specific to the unique risks accountants face. Focus on real world scenarios they encounter daily such as phishing attempts through email, protecting client tax documents, securing remote access platforms, and maintaining confidentiality during virtual consultations. Use interactive workshops, simulated cybersecurity challenges, and role playing exercises that demonstrate exactly how cyber threats could impact their work and clients. Consider creating video tutorials, quick reference guides, and short testing modules that help your team understand and retain critical security protocols.
Implement a continuous learning approach by scheduling quarterly refresher training sessions and sending monthly cybersecurity updates. Track participation and comprehension through quick online assessments that reinforce key concepts. Recognize and reward team members who demonstrate strong security practices to encourage a culture of proactive cybersecurity awareness.
Pro tip: Design your training materials using scenario based learning that reflects actual Miami accounting firm challenges, making the content immediately relevant and engaging for your specific professional context.
To help design higher-impact team training, here is a quick comparison of common cyber threats and suggested response strategies specific to accounting firms:
| Threat Type | Example Scenario | Recommended Team Response |
|---|---|---|
| Phishing Email | Fake client tax document request | Verify sender before action |
| Ransomware Attack | Malicious link in invoice message | Isolate affected device immediately |
| Data Leak Attempt | Unusual remote access at odd hours | Notify IT and follow escalation plan |
| Social Engineering | Call requesting client credentials | Decline request and report up chain |
Step 3: Implement security policies and practical safeguards
Developing robust security policies is critical for protecting your Miami accounting firm from potential cyber threats. Integrating qualitative and quantitative approaches to measure and manage cyber risk provides a comprehensive strategy for creating effective safeguards that address both technical and human factors in cybersecurity.
Start by establishing clear written guidelines that cover every aspect of digital security. This includes password management protocols, email communication standards, client data handling procedures, and remote work security requirements. Create specific rules about device usage, network access, and acceptable software installations. Implement multi factor authentication for all critical systems, require regular password changes, and set up automatic software update mechanisms to ensure your technological defenses remain current.
Establish a continuous threat exposure management framework that allows your firm to dynamically assess and respond to emerging cybersecurity risks. This means conducting regular security audits, maintaining an updated inventory of all digital assets, and developing rapid response protocols for potential security incidents. Develop clear escalation procedures that outline exactly what steps team members should take if they detect a potential security breach or suspicious activity.
Pro tip: Create a compact security quick reference card that team members can keep at their workstations, summarizing key policies, emergency contact information, and critical security procedures in an easy to understand format.
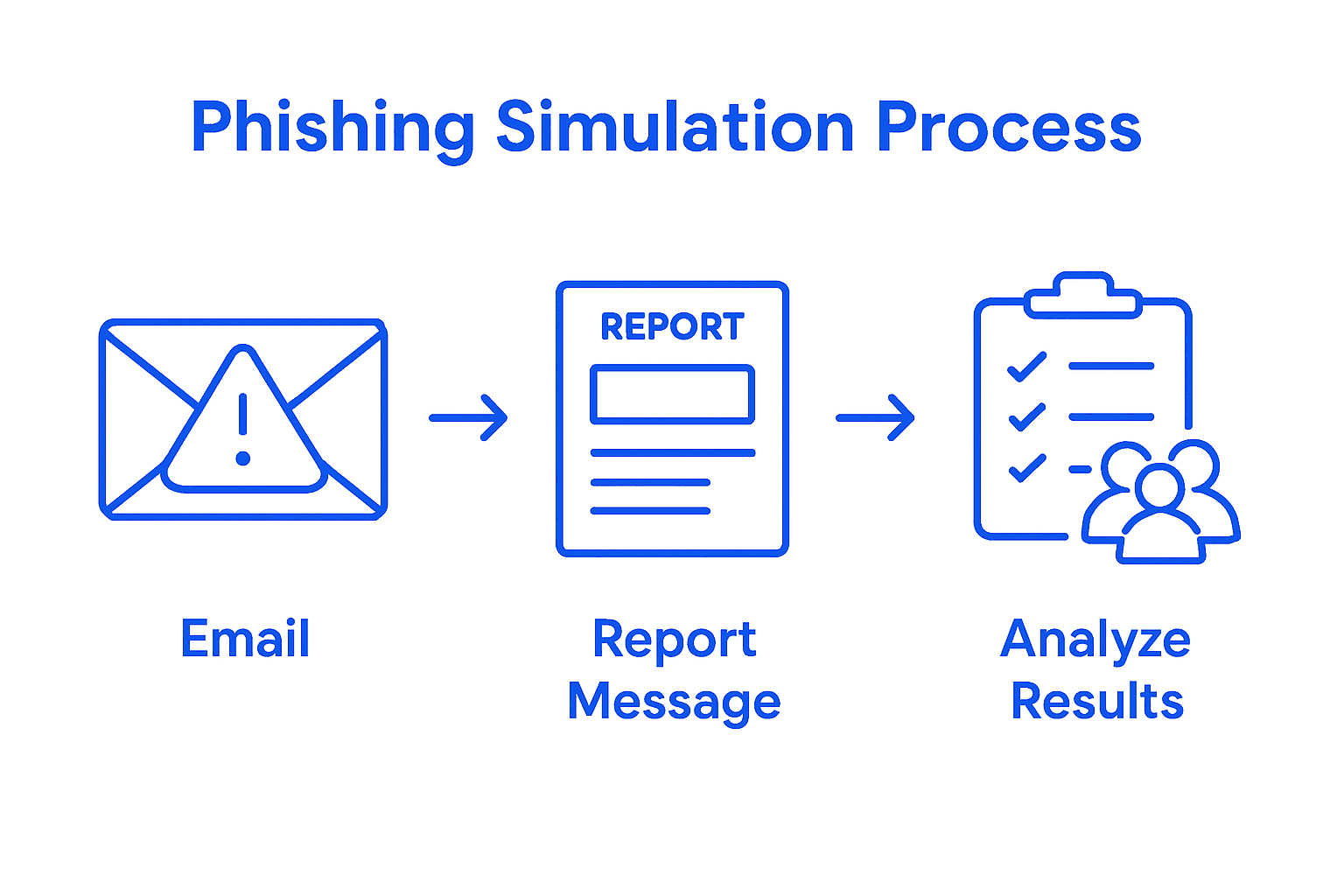
Step 4: Reinforce learning with simulated phishing exercises
Simulated phishing exercises are a powerful way to transform theoretical cybersecurity knowledge into real world defensive skills for your accounting team. By creating controlled scenarios that mimic actual cyber threats, you can help your staff develop muscle memory for identifying and responding to potential security risks before they become genuine problems.
Design a series of realistic phishing simulations that reflect the specific types of email attacks common in financial services. Create scenarios that look like legitimate client communications, tax document requests, or professional network invitations. These exercises should test your team’s ability to recognize suspicious sender addresses, unusual attachment types, unexpected links, and requests for sensitive information. Track individual and team performance carefully, providing immediate feedback and personalized training for team members who click on simulated phishing links or accidentally share sensitive information.
Make these exercises a regular part of your cybersecurity training program, conducting simulations quarterly and varying the complexity and style of potential threats. Use the results to identify systemic vulnerabilities, develop targeted training modules, and build a culture of continuous learning and vigilance. Reward team members who consistently demonstrate strong security awareness, creating positive reinforcement that encourages proactive defense against potential cyber threats.
Pro tip: Rotate simulation scenarios to keep your team engaged and prevent them from becoming predictable, ensuring that cybersecurity training remains challenging and relevant to emerging threat landscapes.
Step 5: Verify progress through periodic assessment and feedback
Developing a systematic approach to estimate and analyze your cybersecurity infrastructure is critical for maintaining robust defense mechanisms in your Miami accounting firm. Periodic assessments allow you to transform theoretical security strategies into measurable, actionable insights that continuously improve your organization’s cyber resilience.
Create a comprehensive assessment framework that goes beyond simple checklist evaluations. Conduct quarterly cybersecurity performance reviews that include detailed metrics such as team response times during simulated attacks, individual and collective phishing test results, policy compliance rates, and rapid incident reporting performance. Implement anonymous feedback mechanisms that encourage team members to share their perspectives on current security protocols, potential vulnerabilities they have observed, and suggestions for improvement without fear of professional repercussions.
Utilize continuous threat exposure management techniques to dynamically track and adapt your security posture. This means not just measuring current performance but actively identifying emerging risks, tracking remediation progress, and creating a living documentation of your firm’s cybersecurity evolution. Generate clear, digestible reports that demonstrate progress to leadership, highlight areas requiring additional focus, and provide transparent evidence of your ongoing commitment to protecting client information.
Pro tip: Develop a scoring system that gamifies cybersecurity performance, allowing team members to track their individual and collective security awareness progress in a motivating and engaging manner.
Strengthen Your Miami CPA Firm’s Cybersecurity with Expert Guidance
The article highlights the critical challenges Miami CPAs face in protecting sensitive financial data through tailored awareness training and ongoing risk assessments. Cybersecurity threats like phishing, ransomware, and social engineering can seriously jeopardize your client trust and firm reputation. Addressing these pain points requires a proactive approach that combines technology, continuous education, and practical safeguards.
Take your cybersecurity readiness to the next level with proven strategies from our Security Archives – Stratgetic IT Consultants For Accountants.
Explore how our expert solutions help you build the capabilities and compliance your clients expect while scaling your firm without adding proportional hiring burdens. Visit https://www.transform42inc.com/ today to regain control over your firm’s security posture. Discover how integrating best practices from the Grc Archives – Stratgetic IT Consultants For Accountants can empower your team to defend against evolving cyber threats effectively.
Frequently Asked Questions
What are the first steps to assess cybersecurity risks for my CPA firm?
Begin by creating a comprehensive inventory of all digital assets and systems used in your firm. Map out how sensitive data flows between these systems and identify potential vulnerabilities.
How can I create effective cybersecurity training for my accounting team?
Develop tailored training modules that address the specific threats encountered by accountants, such as phishing and data leaks. Incorporate real-world scenarios and interactive exercises to engage the team and reinforce best practices.
What security policies should be implemented to protect client information?
Establish clear guidelines for password management, email communication, and remote access. Implement multi-factor authentication and regular software updates to strengthen your firm’s overall security posture.
How often should I conduct phishing simulations for my team?
Conduct phishing simulations quarterly to help your staff practice identifying and responding to potential threats. Vary the scenarios to keep the exercises relevant and challenging.
What metrics should I track to measure cybersecurity awareness progress?
Track key performance indicators such as team response times during simulated attacks and individual phishing test results. Conduct quarterly reviews to evaluate improvements and adjust training strategies as needed.
How can I foster a culture of cybersecurity awareness among my staff?
Encourage a proactive approach by recognizing and rewarding team members who demonstrate strong security practices. Implement continuous learning opportunities, such as monthly updates and refresher training sessions, to keep cybersecurity at the forefront of employees’ minds.